Short on howto setup a default SSL server config for nginx.
Sometimes a webserver is required for some reason. Those times SSL/TLS is also usually required. Some of those times a shared server is used.
For quite some time now SNI (Server Name Indication) has been there to make this work.
However, all virtual hosts must be named for a certificate to be valid. So what happens if you visit the server by https://IP? It usually spits out a warning about the name mismatch and then returns the first configured SSL vhost.
This is not always a wanted behaviour as it can leak information and if nothing else just looks bad.
You can solve this by generating a mostly empty certificate with openssl and adding that to the default ssl server in nginx with a 444 response which closes the connection. Not all fields can be empty for openssl to accept the request but most can and you can always leave some default suggestions too.
root@www:/root # openssl req -x509 -nodes -days 999 -newkey rsa:2048 -keyout /usr/local/etc/nginx/ssl/default.key -out /usr/local/etc/nginx/ssl/default.crt
So both default_servers now look like this config example;
server {
server_name _;
listen 80 default_server;
return 444;
}
server {
server_name _;
listen 443 ssl default_server;
return 444;
ssl_certificate /usr/local/etc/nginx/ssl/default.crt;
ssl_certificate_key /usr/local/etc/nginx/ssl/default.key;
include ssl.include;
}Verify with nginx -t before restarting the service to make sure there are no issues.
When validating with curl you can see I kept the default Internet Widgits Pty Ltd and Some-State but left the rest blank.
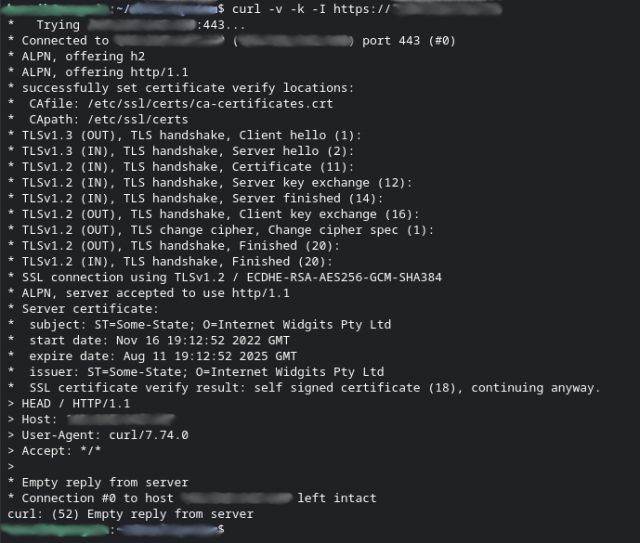
I think this is reasonable opsec procedure for anyone even when not particularly trying to hide things.
Examples are from a FreeBSD machine so ymmv regarding paths etc.
