Getting persistent root in a few simple steps by dumping the filesystem directly from the memory chip of an IP camera.
This is a short write up of a presentation I gave during spring and summer at among others 2600 Malmö that was in turn based on this very draft of working with a particular camera, so excuse the choppy writing while I somewhat go full circle.
An IP camera is just an embedded Linux system running on an SoC with varyingly capable optics on top of it. This makes life easier for most people as familiarity with Linux is common to say the least.
After opening the camera I found the memory chip - pink box - (not many DIP-8 chips on the board). The red wire on the clip goes to pin 1 on both reader and chip, keep track of it! In this case denoted by the small indent seen on the top right of the IC package. Other markings is sometimes a white dot or an indentation in one of the non pin sides, find the spec if you are unsure. Just googling the text on the chip usually leads to it.
Also worth mentioning is the UART connection - green box - that can be used like any other serial console, good to have once we have credentials for the camera. You can also dump the firmware via UART, but that is for another time.
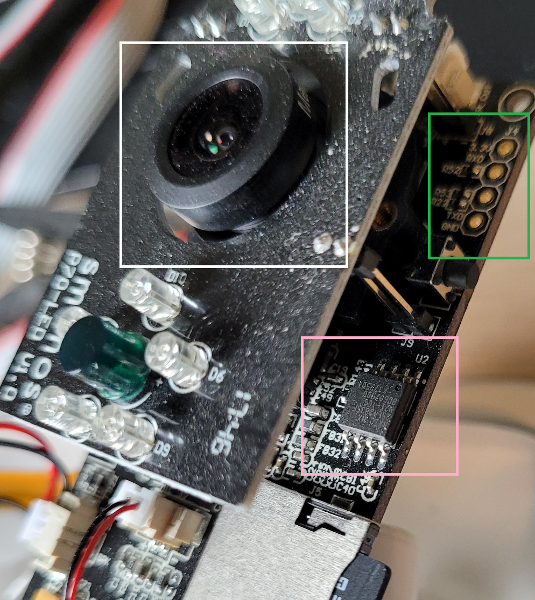
I then proceeded to bend the camera package out of the way to be able to access it with the reader.
 Purchase an EEPROM programmer with SOIC test clip on aliexpress here - please note that this is a referral link.
Purchase an EEPROM programmer with SOIC test clip on aliexpress here - please note that this is a referral link.
After connecting the test clip to the chip and fiddling around with getting a proper seating I ran a full dump of it.
sudo flashrom --programmer ch341a_spi -c MX25L12835f/MX25L12845E/MX25L12865E -r new.bin
I did this on a chromebook in the virtual linux environment after simply installing the flashrom package, your mileage may vary.
Just to be clear, this is not really the proper way to do a dump of the firmware, but a rather crude and quick one. As most embeddeds have two partitions used for updates, resets and teh like this gets everything twice. It also pulls any other data that might be on the chip.
The next step is unpacking the file system with binwalk
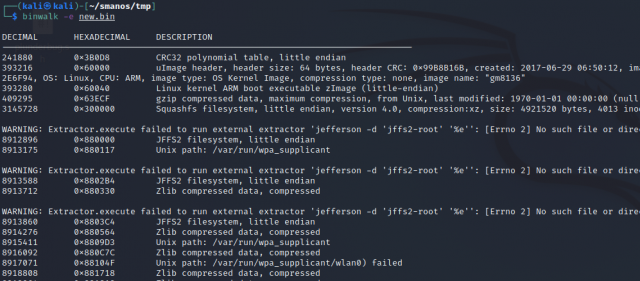 As mentioned above the dump contains data that is useless to us for this but it gets us what is needed.
As mentioned above the dump contains data that is useless to us for this but it gets us what is needed.
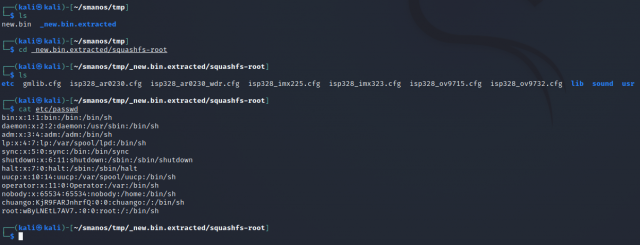
And the last step, cracking the passwords.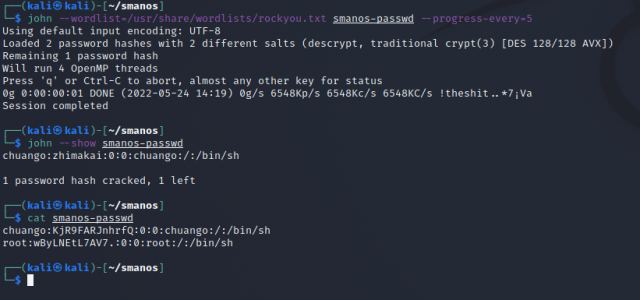 Here I used john and the rockyou wordlist to successfully crack one of the root accounts, I did not bother to continue with the second as I just wanted the access in this case.
Here I used john and the rockyou wordlist to successfully crack one of the root accounts, I did not bother to continue with the second as I just wanted the access in this case.
And that is that, camera put together again and full root achieved with no damage or signs of tampering!
So if we actually wanted to write data back to the chip the -w flag for flashrom will do that. But then a proper dump of one data partition should be the starting point to not brick the device.
